The Update Framework

The Update Framework (TUF) is a software framework designed to protect mechanisms that automatically identify and download updates to software. TUF uses a series of roles and keys to provide a means to retain security, even when some keys or servers are compromised. It does this with a stated goal of requiring minimal changes and effort from repository administrators, software developers, and end users. In this way, it protects software repositories, which are an increasingly desirable target for hackers.
A software update, sometimes referred to as a patch, can add functionalities and address flaws in existing code. Unfortunately, in delivering updates to neutralize flaws, these systems can unintentionally introduce vulnerabilities that, in turn, can be exploited by attackers.
The design of TUF acknowledges that all software repositories will likely be compromised at some point, so any security strategy must be prepared for that scenario. TUF-enabled systems focus on limiting the impact of attacks and providing a mechanism for recovery. This strategy of “compromise-resilience” improves on existing methods based on keysigning by incorporating techniques, such as separation of signing duties and setting a threshold number of required signatures. Dividing the responsibility for authenticating a file or image ensures no single hacker can compromise the system. It also helps to ensure that keys used to perform a sensitive action can be stored in a secure, offline manner. Even if one party—or the repository itself—is compromised, the number of projects affected will be limited.
To date, the list of tech companies and organizations using TUF include IBM, VMware, Digital Ocean, Microsoft, Google, Amazon, Leap, Kolide, Docker, and Cloudflare.
TUF design :
The Update Framework (TUF) design helps developers maintain the security of a software update system, even against attackers that compromise the repository or signing keys. TUF provides a flexible specification defining functionality that developers can use in any software update system or re-implement to fit their needs.
TUF is hosted by the Linux Foundation as part of the Cloud Native Computing Foundation (CNCF) and its design is used in production by various tech companies and open source organizations. A variant of TUF called Uptane is used to secure over-the-air updates in automobiles.
What they are trying to do?
There are literally thousands of different software update systems in common use today. In fact the average Windows user has about two dozen different software updaters on their machine
They are building a library that can be universally (and in most cases transparently) be used to secure software update systems.
What Is a Software Update System?
Generally, a software update system is an application (or part of an application) running on a client system that obtains and installs software. These systems typically update the applications installed on client systems to introduce new features, enhancements, and security fixes.
Three major classes of software update systems are:
- Application updaters which are used by applications to update themselves. For example, Firefox updates itself through its own application updater.
- Library package managers such as those offered by many programming languages for installing additional libraries. These are systems such as Python's pip/easy_install + PyPI, Perl's CPAN, Ruby's RubyGems, and PHP's Composer.
- System package managers used by operating systems to update and install all of the software on a client system. Debian's APT, Red Hat's YUM, and openSUSE's YaST are examples of these.
Overview
On the surface, the update procedure followed by a software update system can be regarded as straightforward. Obtaining and installing an update just means:
- Knowing when an update exists.
- Downloading the update.
- Applying the changes introduced by the update.
The problem with this view is that it is only straightforward when there are no malicious parties involved throughout the update procedure. If an attacker is trying to interfere with these seemingly simple steps, there is plenty that they can do.
TUF is designed to perform the first two steps of the above update procedure, while guarding against the majority of attacks that malicious actors have at their disposal; especially those attacks that are overlooked by security-conscious developers.
Background
Let's assume we take the approach that most systems do (at least, the ones that even try to be secure). We download both the file we want and a cryptographic signature of the file. We already know which key we trust to make the signature. We check that the signature is correct and was made by this trusted key. All seems well, right? Wrong. We are still at risk in many ways, including:
- An attacker keeps giving us the same file, so we never realize there is an update.
- An attacker gives us an older, insecure version of a file that we already have, so we download that one and blindly use it thinking it's newer.
- An attacker gives us a newer version of a file we have but it's not the newest one. It's newer to us, but it may be insecure and exploitable by the attacker.
- An attacker compromises the key used to sign these files and now we download a malicious file that is properly signed.

These are just some of the attacks software update systems are vulnerable to when only using signed files. See Security for a full list of attacks and updater weaknesses TUF is designed to prevent.
The following papers provide detailed information on securing software updater systems, TUF's design and implementation details, attacks on package managers, and package management security:
- Mercury: Bandwidth-Effective Prevention of Rollback Attacks Against Community Repositories https://theupdateframework.io/papers/attacks-on-package-managers-ccs2008.pdf
- Diplomat: Using Delegations to Protect Community Repositories https://theupdateframework.io/papers/protect-community-repositories-nsdi2016.pdf
- Survivable Key Compromise in Software Update Systems https://theupdateframework.io/papers/survivable-key-compromise-ccs2010.pdf
- A Look In the Mirror: Attacks on Package Managers https://theupdateframework.io/papers/package-management-security-tr08-02.pdf
- Package Management Security https://theupdateframework.io/papers/attacks-on-package-managers-ccs2008.pdf
What TUF Does?
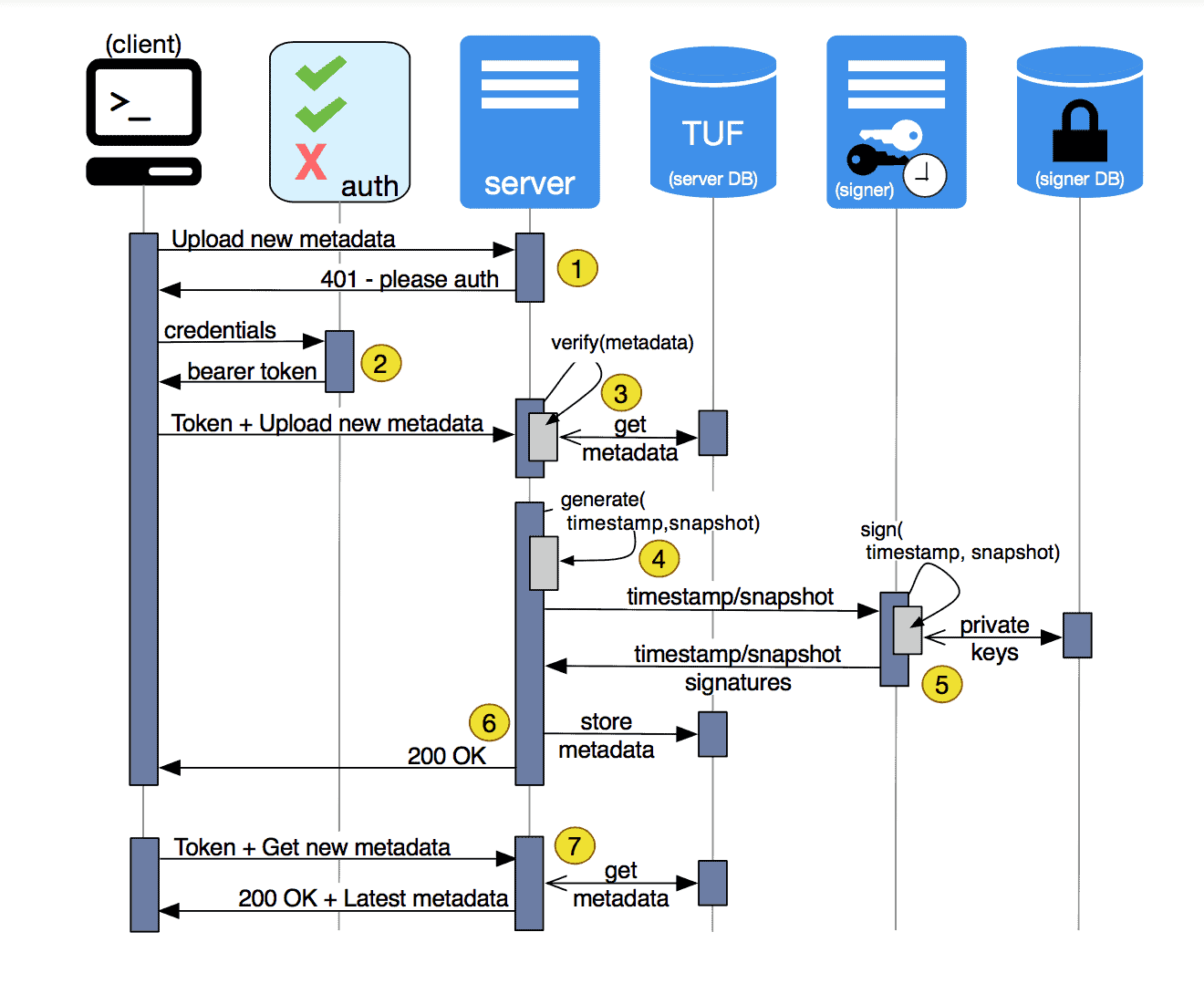
In order to securely download and verify target files, TUF requires a few extra files to exist on a repository. These are called metadata files. TUF metadata files contain additional information, including information about which keys are trusted, the cryptographic hashes of files, signatures on the metadata, metadata version numbers, and the date after which the metadata should be considered expired.
When a software update system using TUF wants to check for updates, it asks TUF to do the work. That is, your software update system never has to deal with this additional metadata or understand what's going on underneath. If TUF reports back that there are updates available, your software update system can then ask TUF to download these files. TUF downloads them and checks them against the TUF metadata that it also downloads from the repository. If the downloaded target files are trustworthy, TUF hands them over to your software update system. See Metadata for more information and examples.
How TUF improves Software Distribution Security?
In recent years that there been multiple cyber-attacks that compromised a software developer’s network to enable the delivery of malware inside of software updates.
TUF defines an system in which software updates are cryptographically signed and secured in a validated way to help minimize the risk of software tampering. There have been multiple incidents in recent years, including one involving cCleaner, in which attackers were able to infiltrate and compromise development systems to send malicious updates to users.

TUF became a Cloud Native Computing Foundation (CNCF) project in October 2017, alongside the Notary project. The CNCF is a Linux Foundation Collaborative Project and is home to multiple technology projects including the Kubernetes container orchestration system. Cappos said that being part of the CNCF has helped to advance the TUF project, in terms of having proper governance and validation. The CNCF also helps to promote TUF and the work that the project is doing.